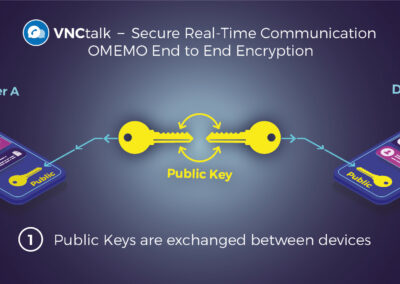
High security is usually associated with specific areas of application such as critical infrastructure, the banking sector or public institutions. Strictly speaking, however, it is a topic that should concern every company and every decision-maker, since it stands for nothing less than digital sovereignty in the social and economic sphere. Behind this are characteristics such as the transparency of data flows, the resilience of the infrastructure, and the control over the platforms, solutions, and devices used. In order for companies and institutions to harden their IT, high security must be implemented in the process before software development even begins. VNC, a leading developer of open source-based enterprise applications, presents five aspects that characterize highly secure software development.
- Secure platform and infrastructure: Ideally, high security as a requirement for software development should already be taken into account when deciding on a platform and its associated infrastructure components. This can only succeed if SecOps experts are involved in the initial phase. A highly secure software cannot be implemented and made available on a platform that is not compatible with SecOps criteria because, for example, it does not allow a transparent view of the code. Since from a legacy perspective many companies do not want to disruptively migrate their existing environment to an open source Kubernetes, some compromise is often necessary. For example, existing clouds and user admins can remain integrated into the IT system via interfaces, but without any data from the high-security components being transmitted to them.
- More interdisciplinary work on code: Programming high-security software requires a clear rethinking of teamwork. It is not a good strategy to let programmers do their work and then attempt to integrate security aspects through code controlling. For this reason, software development must involve interdisciplinary work with DevOps and SecOps experts right from the start, who can immediately name the effects of components on data processing, interfaces or security. This requires close exchange and permanent interdisciplinary work on the code.
- Transparency of open source: In order to be able to evaluate the data processing procedures and data security of platforms and technologies in the first place, it is necessary to take a look inside the code. In fact, with proprietary closed-source solutions, this cannot be evaluated from the outside. Vulnerabilities in the software can remain undetected: a problem that starts at the lowest level with an operating system for the router and extends through cloud computing to the application software. At all levels, proprietary systems pose a risk that is difficult to calculate – and that affects the vast majority of all enterprises. The solution to reduce this risk is called open source and refers to software whose code can be viewed. Incidentally, it is also necessary in order to comply with GDPR requirements in a legally secure manner. Open source is the only way to ensure that no black boxes or components integrated in the code can cause a data leak.
- Recurring coding components: EDevelopment teams determined to create all the components they use on their own, following the concept of high security, instead of buying them, are faced with complex processes. To reduce complexity, it is advisable to use recurring coding components. This means that parts of the code are used for many applications, as in a module system – for example, in the graphical representation of certain buttons and user avatars or the definition of actions. This reuse also allows to set up broad product landscapes, which can then be checked for data security in automated tests.
- Automated testing and audits: All theory is gray – in practice however, it is the worst case scenario that shows whether what has been declared as secure is actually secure. For this reason, automated testing of new code sections plays an important role. This makes it possible to check whether certain functions result in security vulnerabilities. Here, too, open source solutions are the only ones offering the advantage of providing transparent insights into the code. At the macro level, load and penetration tests or friendly hacking can also show whether risks are lurking in the infrastructure or individual applications, especially in the high-security area.
“Even before the start of actual software development, the topic of high security should be discussed,” emphasizes Andrea Wörrlein, Managing Director of VNC in Berlin and Board Member of VNC AG in Zug. “This only succeeds when DevOps and SecOps teams work together and join the discussion. After all, there is no point in developing a software without already working out how to run it securely. In the long term, the migration plan should then aim to replace all non-transparent proprietary solutions with open source.”
About VNC – Virtual Network Consult AG
VNC – Virtual Network Consult AG, based in Switzerland, Germany and India, is a leading developer of open source-based enterprise applications and positions itself as an open and secure alternative to the established software giants. With VNClagoon, the organization with its global open source developer community has created an integrated product suite for enterprises, characterized by high security, state-of-the-art technology and low TCO. VNC’s customers include system integrators and telcos as well as large enterprises and institutions.
Further information on https://vnclagoon.com, on Twitter @VNCbiz and on LinkedIn.
Contact
Andrea Wörrlein
VNC – Virtual Network Consult AG
Poststrasse 24
CH-6302 Zug
Phone: +41 (41) 727 52 00
aw@vnc.biz
Beatrice Ferri
PR-COM GmbH
Sendlinger-Tor-Platz 6
80336 München
Phone: +49-89-59997-704
beatrice.ferri@pr-com.de